🌐 3v@l
A detailed write-up of the Web challenge '3v@l' from PicoCTF - 2025
📊 Challenge Overview
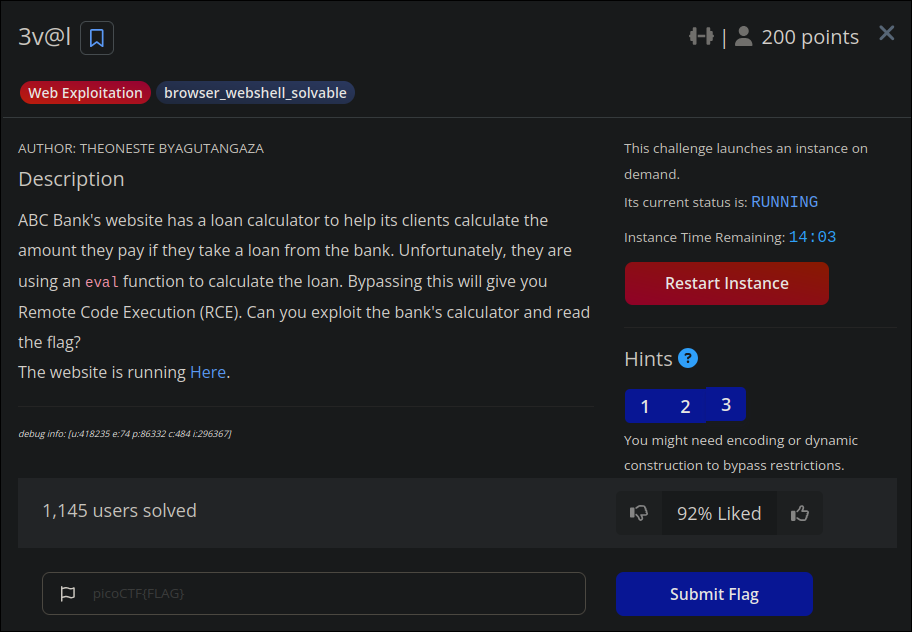
Category Details Additional Info 🏆 Event PicoCTF - 2025 Event Link 🔰 Category Web 🌐 💎 Points 200 Out of 200 total ⭐ Difficulty 🟡 Medium Personal Rating: 1/10 👤 Author Theoneste Byagutangaza Profile 🎮 Solves (At the time of flag submission) 1.145 solve rate 📅 Date 11-03-2025 PicoCTF - 2025 🦾 Solved By mH4ck3r0n3 Team:
📝 Challenge Information
ABC Bank’s website has a loan calculator to help its clients calculate the amount they pay if they take a loan from the bank. Unfortunately, they are using an eval function to calculate the loan. Bypassing this will give you Remote Code Execution (RCE). Can you exploit the bank’s calculator and read the flag?
🎯 Challenge Files & Infrastructure
Provided Files
1Files: None
🔍 Initial Analysis
First Steps
Initially, the website appears as follows:
From the challenge description, we are told that everything we pass is inserted into an
eval()function, which evaluates a string as an expression and executes it if valid. So, I decided to inspect the page source:We are informed that everything is handled in Python with
Flaskand that there are two filters:
- Blocking malicious keywords like
os,eval,exec,bind,connect,python,socket,ls,cat,shell,bind.- Implementing regex:
r'0x[0-9A-Fa-f]+|\u[0-9A-Fa-f]{4}|%[0-9A-Fa-f]{2}|\.[A-Za-z0-9]{1,3}\b|[\/]|\.\.'.So, to achieve RCE, we likely need to bypass these two filters. Reading the hints, we are given additional clues:
- Bypass regex
- The flag file is
/flag.txt- You might need encoding or dynamic construction to bypass restrictions.
Now we know that we need to read the
flag.txtfile located in the/directory. Let’s move on to the exploitation phase.
🔬 Vulnerability Analysis
Potential Vulnerabilities
- RCE (Remote Code Execution)
🎯 Solution Path
Exploitation Steps
Initial setup
For the first filter, we don’t even need to go crazy trying to find ways to use
osto read/flag.txt. In fact, we can directly use the functionopen("/flag.txt").read(). So, we only need to figure out how to bypass the regex. Let’s move on to the next phase.
Exploitation
After a few tests, I noticed that the
/character is filtered by the regex, meaning we can’t pass it in plain text, or we will get the errorError: Detected forbidden keyword ''. The first thing that came to mind was encoding it in hex (\x2f), but the issue is that the check happens beforeeval, and more importantly, after the string has been parsed.So, I decided to use decimal-to-character casting with
chr(). To determine the decimal value of/, I used theord()function:As we can see, it corresponds to
47, so I tried sendingchr(47)as the payload:This successfully returned
/, bypassing the regex. Now that I understood how to bypass the regex, the payload structure would beopen(chr(47)+...).read().I wrote a Python script to generate the payload automatically instead of constructing it manually, applying the same operation for each character in
/flag.txt. The final payload I obtained was:
open(chr(47)+chr(102)+chr(108)+chr(97)+chr(103)+chr(46)+chr(116)+chr(120)+chr(116)).read()By sending this payload, I successfully read the
/flag.txtfile and retrieved the flag.
Flag capture
🛠️ Exploitation Process
Approach
The automatic exploit performs the same steps as the manual one. It sends a POST request to
/executewith the previously seen payload and then extracts the flag from the response using a regex.
🚩 Flag Capture
Flag
Proof of Execution
🔧 Tools Used
Tool Purpose Python Exploit
💡 Key Learnings
Time Optimization
- Always remember the
open()function and the possibility of sending characters aschr()to bypass filters.
Skills Improved
- Binary Exploitation
- Reverse Engineering
- Web Exploitation
- Cryptography
- Forensics
- OSINT
- Miscellaneous
📊 Final Statistics
| Metric | Value | Notes |
|---|---|---|
| Time to Solve | 00:07 | From start to flag |
| Global Ranking (At the time of flag submission) | 2091/9215 | Challenge ranking |
| Points Earned | 200 | Team contribution |
Created: 11-03-2025 • Last Modified: 11-03-2025 *Author: mH4ck3r0n3 • Team: *