🌐 WebSockFish
A detailed write-up of the Web challenge 'WebSockFish' from PicoCTF - 2025
📊 Challenge Overview
Category Details Additional Info 🏆 Event PicoGym Event Link 🔰 Category Web 🌐 💎 Points Out of 500 total ⭐ Difficulty 🟡 Medium Personal Rating: 2/10 👤 Author Venax Profile 🎮 Solves (At the time of flag submission) 1.321 solve rate 📅 Date 20-03-2025 PicoGym 🦾 Solved By mH4ck3r0n3 Team:
📝 Challenge Information
Can you win in a convincing manner against this chess bot? He won’t go easy on you!
🎯 Challenge Files & Infrastructure
Provided Files
1Files: None
🔍 Initial Analysis
First Steps
Initially, the website appears as follows:
the first thing I thought of was using
stockfishto beatstockfish, but after winning the game, I didn’t get any flag. So I started looking for other ways to win the game. Inspecting the source of the page, I noticed that everything is managed client-side, andwebsocketsare used to communicate withjs/stockfish.min.js:
1 2 3 4 5 6 7 8 9 10 11 12 13var ws_address = "ws://" + location.hostname + ":" + location.port + "/ws/"; const ws = new WebSocket(ws_address); ws.onmessage = (event) => { const message = event.data; updateChat(message); }; function sendMessage(message) { ws.send(message); } function updateChat(message) { const chatText = $("#chatText"); chatText.text(message); }so far, the most interesting function is
updateChat(message), since it is the function that I assume changes the stockfish message, as seen in the previous screenshot. Intuitively, I think that’s where we somehow need to retrieve the flag. Continuing to read, I found the function that stockfish uses to handle messages:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20stockfish.onmessage = function (event) { var message; // console.log(event.data); if (event.data.startsWith("bestmove")) { var bestMove = event.data.split(" ")[1]; var srcSq = bestMove.slice(0, 2); var dstSq = bestMove.slice(2, 4); var promotion = bestMove.slice(4); game.move({ from: srcSq, to: dstSq, promotion: promotion }); board.position(game.fen()); } else if (event.data.startsWith(`info depth ${DEPTH}`)) { var splitString = event.data.split(" "); if (event.data.includes("mate")) { message = "mate " + parseInt(splitString[9]); } else { message = "eval " + parseInt(splitString[9]); } sendMessage(message); } };since we can send messages using the
ws.send("message")function (as written in thesendMessage()function seen earlier), I started testing. In fact, by sendingbestmoveas a message, the stockfish text shouldn’t change based on the function just seen:as we can see, the
sendMessage(message)function is not called, and the message remains unchanged. Now let’s try withmate:as we can see,
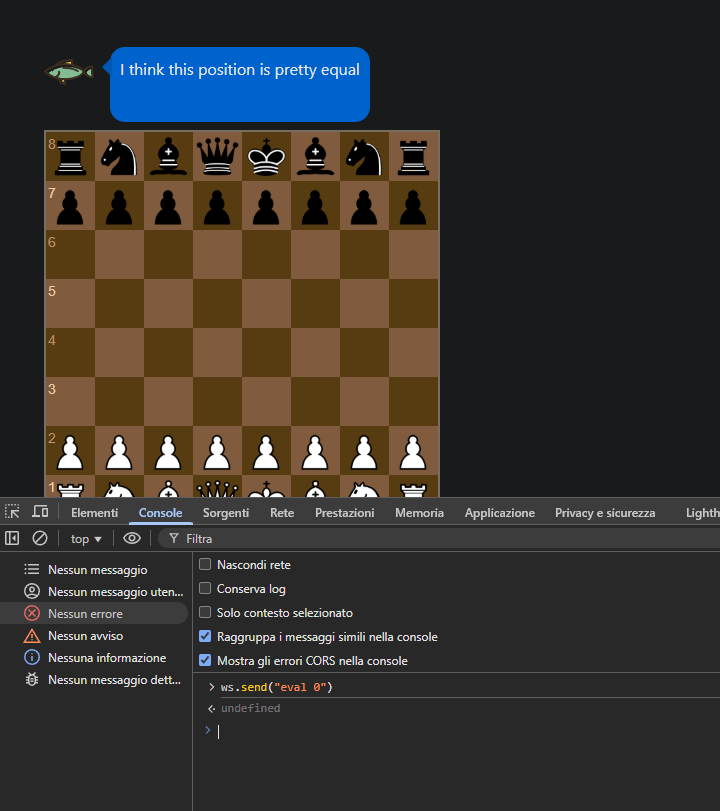
stockfishinterprets the messagemate 0as checkmate in zero moves. However, in a situation where checkmate does not occur,eval xis sent. Let’s see what thisevaldoes:by sending
eval 0, I get the messageI think this position is pretty equal. From here, it can be inferred thateval xchanges the stockfish message as we move pieces, analyzing the game, and the message will be adjusted based on how the game is going. In case of a disadvantage, it will say something related to it, and similarly in case of an advantage. Let’s move on to the exploitation phase.
🎯 Solution Path
Exploitation Steps
Initial setup
As mentioned earlier, the flag will most likely be contained in the messages from
stockfish, so I wondered, since sending0results in an equal position, what would happen if I sent9999?Given the message
You're in deep water now!, I imagine that with positive numbers, it seems stockfish believes it has an advantage, and consequently, I think that with negative numbers, it would think it is at a disadvantage.
Exploitation
So I initially tried with low negative numbers since I didn’t know how far stockfish’s scoring goes. Later, when I sent
-99999, stockfish responded with the flag message, thinking it was at such a big disadvantage that it forced it to surrender.
Flag capture
🛠️ Exploitation Process
Approach
The automatic exploit connects to a
websocket, sends the messageeval -99999, captures the response, and extracts the flag from it using a regex.
🚩 Flag Capture
FlagpicoCTF{c1i3nt_s1d3_w3b_s0ck3t5_e5e75e69}
Proof of Execution
🔧 Tools Used
Tool Purpose Python Exploit WebDevTools Web Testing
💡 Key Learnings
Time Optimization
- Try to understand how things work with some testing.
Skills Improved
- Binary Exploitation
- Reverse Engineering
- Web Exploitation
- Cryptography
- Forensics
- OSINT
- Miscellaneous
📚 References & Resources
Learning Resources
📊 Final Statistics
| Metric | Value | Notes |
|---|---|---|
| Time to Solve | 00:10 | From start to flag |
| Global Ranking (At the time of flag submission) | Challenge ranking | |
| Points Earned | Team contribution |
Created: 20-03-2025 • Last Modified: 20-03-2025 *Author: mH4ck3r0n3 • Team: *